If you’re asking is walletconnect safe, the short answer is: Yes, WalletConnect is generally safe as a connection and session protocol, but most losses happen because of phishing, malicious approvals, and fake sessions, not because WalletConnect itself was “hacked.”
WalletConnect v2 is simply a communication layer between wallets and decentralized applications (dApps). It does not custody funds, store private keys, or execute transactions on its own. The real risk emerges when users approve malicious requests or when wallets fail to validate session proposals properly.
This guide provides a practical, opinionated WalletConnect v2 security checklist for:
Just real-world risk models and actionable mitigation steps.
If you only read one section, read this.
WalletConnect is generally safe because:
WalletConnect becomes risky when:
What users should do today:
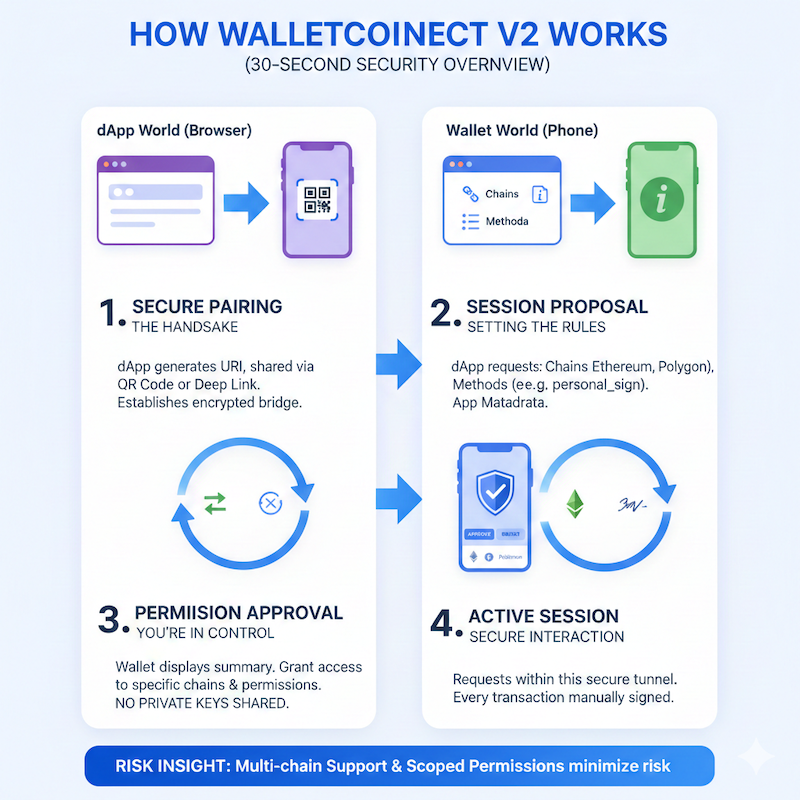
Understanding risk starts with understanding flow.
1. Secure Pairing (The Handshake) The dApp generates a unique URI, shared via QR Code or Deep Link. This initiates a secure connection between the wallet and the dApp, typically routed via a Relay Server. Data between the wallet and the dApp is protected with end-to-end encryption (E2EE), so the relay does not see the message content (it only forwards encrypted payloads).
2. Permission Approval (You’re in Control) Your wallet displays a clear summary of these requests. You grant access only to the specific chains and permissions you trust. No private keys are ever shared.
3. Active Session (Secure Interaction) Once approved, the dApp sends requests to your wallet within this encrypted session. Every transaction still requires manual signing by you before it can be submitted to the blockchain.
WalletConnect security issues are almost never protocol failures. They are:
A cloned site prompts users to connect. The session is legitimate — the website is not.
Users sign transactions approving unlimited token allowances. Funds get drained later.
Improperly understood personal_sign or eth_signTypedData requests can authorize harmful actions.
Users stay connected for weeks. The dApp later pushes a malicious request.
Session proposals show generic or misleading names/icons.
| Risk | What It Looks Like | Mitigation |
|---|---|---|
| Phishing site | Looks like real dApp, different domain | Verify domain before session approval |
| Unlimited token approval | “Approve spending” without limit | Warn clearly about unlimited allowances |
| Blind signature | Raw hex data signing | Display decoded signing data |
| Long-lived session | Always connected | Auto-expire sessions + visible disconnect UI |
| Fake QR code | QR from Discord/Telegram | Validate WalletConnect URI structure |
Common walletconnect phishing patterns include:
Users should:
Do this
Avoid this
Remember: a walletconnect scam works because the user approves something harmful — not because WalletConnect was breached.
If you’re building a wallet, WalletConnect integration must be treated as a security-critical surface.
WalletConnect v2 session permissions are aligned with CAIP-25, a chain-agnostic standard that helps structure how wallets and apps describe accounts, chains, and requested capabilities across ecosystems. In practice, this is why v2 can support richer multi-chain sessions and more granular permissions and why your validation logic must be strict at the “session proposal” boundary.
Implement walletconnect verify api integration.
Treat status as:
Never silently approve unknown origins.
For walletconnect deep link security:
Never trust raw QR input.
Validate:
This reduces spoofing.
Do not auto-approve all methods.
Use:
If dApp only needs eth_sign, don’t approve eth_sendTransaction.
Only approve required event subscriptions. Overexposure increases attack surface.
Implement:
Clear session management is critical for walletconnect session management security.
Trigger enhanced warnings for:
Explain clearly in human-readable language.
Wallet teams should log:
Rate limit abuse patterns.
If you’re implementing WalletConnect inside a consumer wallet, your architecture matters.
Explore:
For wallet model differences, see:
Trust Wallet vs MetaMask (wallet model comparison) → /trust-wallet-vs-metamask/
Security is shared responsibility.
Poor dApp UX increases wallet risk.
For walletconnect QR code phishing and deep links:
Users must see and approve everything.
Two major request types:
eth_signTypedData security risks arise when users sign structured data without understanding consequences (e.g., off-chain permit signatures).
personal_sign security issues arise when wallets show raw hex blobs without decoding.
Wallets must:
Users should:
If you think something went wrong:
Time matters. Act quickly.
Yes, when implemented correctly. Most losses occur due to phishing and malicious approvals.
No. It cannot move funds without your explicit signature approval.
A verification system that checks dApp domain authenticity before session approval.
Use your wallet’s session management section and manually disconnect active sessions.
It depends on what you are signing. Typed data and blind messages can authorize dangerous actions.
Verify domains, reject unknown sessions, avoid signing unclear messages, and disconnect unused sessions.
So, is walletconnect safe?
Yes, WalletConnect v2 is designed as a secure connection layer, including end-to-end encryption (E2EE) between wallet and dApp. The Relay Server routes messages but does not see the message content.
WalletConnect v2 provides powerful tools. Security depends on how responsibly they are used.
If you’re building a wallet and want secure WalletConnect v2 integration aligned with modern multi-chain architecture, review: