A trust wallet clone script is commonly delivered as a ready-to-launch, white-label wallet package: a branded app with the core flows and modules people associate with Trust Wallet—self-custody onboarding, multi-chain assets, Web3 connectivity, and a production release setup.
This guide keeps the discussion practical: what “clone script” means, what’s included vs optional, why teams choose this approach, how revenue typically works, what the architecture looks like, what affects estimates, and why ND Labs is a strong delivery partner.
If you need a quick baseline definition for internal stakeholders, here’s a short explainer on what a crypto wallet is
In practice, “clone script” is an industry label for a packaged wallet foundation that follows a mainstream pattern: create a wallet, back up recovery data, manage assets across networks, send/receive, connect to Web3, confirm actions, and track results. The value is speed and predictability: the baseline UX and core modules are already structured so teams don’t burn months iterating on fundamental screens and flows.
If you want ND Labs to deliver the wallet end-to-end, start here: crypto wallet development services.
A trust wallet clone app model is typically chosen when you need a wallet that can be shipped and marketed as a complete product from day one. It fits three common cases:
1) Branded MVP for a product launch
When a wallet is part of go-to-market (community onboarding, ecosystem access, token utility), you need a baseline that is stable and shippable. A packaged approach reduces time spent on fundamentals and shifts effort to differentiators: supported networks, integrations, analytics, and conversion-focused onboarding.
2) Wallet as a feature inside an ecosystem
In marketplaces and communities, the wallet is often a component rather than the whole business. In this context you’re building a trust wallet alternative wallet under your brand, optimized for your ecosystem: the chains your users need, the integrations that support your revenue model, and a UI consistent with your product.
3) Teams that want predictable scope now and modular growth later
A packaged baseline allows you to launch with a controlled feature boundary and add modules later without destabilizing the core. This is how many teams manage swaps, staking, NFTs, fiat rails, or admin tooling: phase one is stability + onboarding; phase two is monetization and expansion.
Still deciding which wallet model to build? See our comparison: Trust Wallet vs MetaMask (security, chains, and best use cases)
A typical launch baseline includes self-custody onboarding (create/import), secure local key handling, consistent signing and confirmation UX, and daily operations: portfolio, send/receive, QR, and transaction history. On Web3, the baseline usually includes WalletConnect; an embedded browser is optional. A dApp browser wallet adds surface area and security UX obligations, so it should be enabled deliberately rather than “because competitors have it.”
Platform scope should also be explicit. Shipping trust wallet clone script for iOS & Android is common, but it’s not a checkbox, it’s a release scope that includes device-level security behavior, QA depth, and store readiness.
Optional modules usually fall into three buckets:
| Feature | Basic Clone | Custom Pro Version |
| Deployment Time | 1-2 Weeks | 4-8 Weeks |
| Supported Chains | ETH, BNB Chain, Polygon | All EVM + Solana & Bitcoin |
| DApp Browser | Included | Fully Custom + Bookmarks |
| Security Audit | Standard | Deep Smart Contract Audit |
| Custom UI/UX | Template-based | 100% Unique Design |
A ready-to-launch package is not only about “building faster.” It’s about reducing execution risk in the highest-friction parts of wallet delivery: baseline UX, release readiness, and operational stability.
Faster time-to-market with a defined baseline
The baseline screens and flows (create/import, backup, send/receive, chain switching, connect & sign) are where teams often lose weeks. A productized package compresses that timeline because the UX patterns and modules are already structured.
More predictable scope and acceptance criteria
“From scratch” projects frequently expand mid-build as stakeholders realize what “a real wallet” must include. With a packaged foundation, it’s easier to define what is in-scope at launch, what is phase two, and what “done” means.
Lower long-term rework risk
Wallets don’t fail only at launch—they fail during iteration when the base is fragile. A packaged foundation is designed to be extended module-by-module, so you can add swaps, NFTs, or new networks without rewriting core flows.
Cleaner brand launch
White-label delivery lets you launch under your brand while keeping mainstream UX patterns. That’s especially useful if you’re positioning a trust wallet like wallet experience for a niche audience (community, region, product ecosystem) and want familiarity without looking generic.
Operational readiness from day one
A proper trust wallet clone script offer should include release discipline (build signing, environment separation, versioning practices) and basic observability so the product can be operated, supported, and improved after launch.
Monetization should be scoped the same way features are scoped: what is in MVP, what depends on partners, and what requires additional compliance or support processes. The most common revenue streams are straightforward, but they need clean integration and clear UX.
Swap fees / routing commissions
If you include swaps, revenue typically comes from routing fees or partner commissions. This is sensitive to the swap provider, supported networks, and quote quality, so it should be treated as a product module with its own QA and monitoring.
On-chain transaction fees (service fees)
Some products add a service fee on top of network fees (where allowed and where UX is transparent). This can work, but it must be designed carefully to avoid trust issues and store review friction.
Staking revenue share
If staking is included, monetization often comes from a share of staking rewards or partner commissions. The implementation scope depends on chains, staking providers, and the UI/UX you want around lockups, rewards, and risk messaging.
Fiat on/off ramp referrals
If fiat rails are included, revenue is often referral-based or volume-based via providers. This stream is usually compliance- and region-dependent, so it should be considered an add-on module, not a default promise.
Promoted dApps / featured listings
If you include discovery sections or browsing, some wallets monetize via sponsored placements. This should be handled carefully so the product doesn’t look like an ad container and so user trust remains intact.
Premium features
Examples include advanced portfolio tools, alerts, policy controls for teams, or enhanced security UX. These require a clear subscription strategy and careful scope so it doesn’t bloat the MVP.
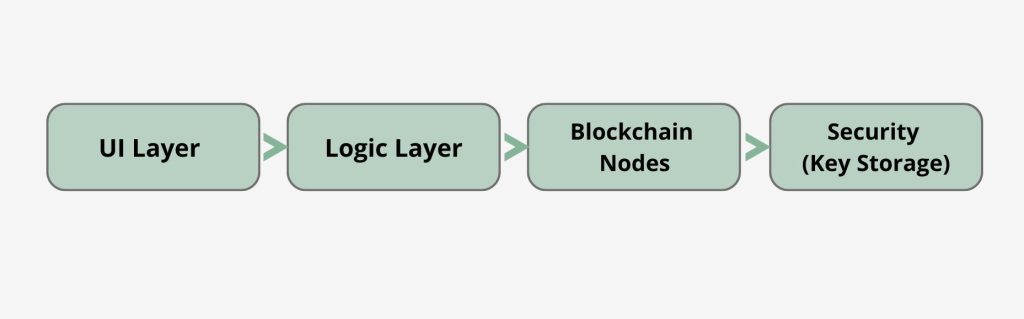
A launch-ready Trust Wallet–like wallet is best described as a set of layers.
Most products ship across iOS and Android, and sometimes add Web later as an additional interface (or an internal admin/dashboard surface). If you plan a multi-platform release, treat it as a real delivery scope: store readiness, QA coverage, and device-level security behavior are part of the launch package.
The wallet operates as a non-custodial HD wallet: keys are generated and stored on the user’s device, and the app signs transactions locally. This layer includes wallet creation/import, seed phrase backup and restore, and a consistent signing/confirmation UX.
Security is implemented primarily through secure key handling and access control. In practice, this means platform-grade storage (Keychain/Keystore and hardware-backed protection where available) plus biometric authentication and PIN-based app lock. Some vendors describe this layer with terms like AES-256 or “2FA,” but the operational requirement is clearer: protect secrets on-device and control access to signing actions with strong UX and release discipline.
Network support is defined by what chains you plan to ship in MVP, for example, Ethereum, Binance Smart Chain, Tron, Polygon, and others. Each added chain expands testing surface (fees, tx types, token discovery) and should be reflected in the scope and timeline.
To keep balances, token metadata, and history consistent, the wallet typically integrates with:
Web3 connectivity is usually delivered via WalletConnect, and optionally an in-app browsing experience, depending on product strategy. If you include a browser, the signing flow becomes the critical safety boundary—clear intent, readable prompts, and post-action traceability.
A common implementation stack for a packaged wallet product includes:
A checklist doesn’t prove readiness. Two flows do.
Acceptance criteria is not “screens exist.” It’s: recovery works, balances are correct for the selected networks, fees display correctly, and the transaction result is traceable in history. If this flow is inconsistent, you’ll see immediate drop-offs and support load.
Baseline requirement is WalletConnect with a readable approval flow. The wallet must show what is being approved, confirm intent, and provide a clear post-action state (submitted / pending / confirmed). This is where a trust wallet like wallet experience is validated in practice.
Security copy tends to drift into buzzwords. A stronger approach is to define baseline controls and delivery practices.
For a short definition you can reuse internally, ND Labs explains non-custodial wallet meaning.
Baseline security should include secure on-device storage for secrets, app access controls (PIN/biometrics), and consistent lock behavior. For Web3, the critical layer is signing UX: readable signing context, consistent confirmations, and guardrails for risky interactions. For send flows, address replacement and clipboard hijack patterns are common enough that UX should include strong confirmation steps and QR-first behavior where it reduces errors.
“Ready-to-launch” should also include secure SDLC practices: scanning in CI, controlled releases, signed builds, and a pentest plan before major milestones. That’s how a trust wallet clone script offer becomes defensible beyond marketing language.
Wallet reliability depends heavily on how balances and history are sourced and updated across networks.
In production, wallets typically rely on RPC providers for chain access, indexing services for efficient history and token data, and caching strategies to reduce rate limits and improve consistency. This layer determines whether portfolio and history stay consistent, whether token discovery behaves predictably, and how the app performs during provider degradation.
When evaluating a trust wallet clone script package, ask for a concrete explanation of provider redundancy, how balances are derived per chain, how token metadata is managed, and how the system behaves during outages. You don’t need proprietary details—just proof that stability is an explicit scope item.
The biggest drivers:
Want exact numbers and packaging? See our Trust Wallet clone app development cost breakdown
A packaged clone foundation is often chosen when you want speed and still need room for customization and modular expansion. A platform-style white-label route tends to be configuration-driven; if you want that productized model, ND Labs’ white label non-custodial crypto wallet page shows what it looks like. From-scratch development is justified when requirements are unusual and cannot be met by a packaged base, with the tradeoff of longer validation and higher upfront execution risk.
If you want a structured framework for packaged solution estimates, see white label crypto wallet pricing.

Most teams don’t need “a clone.” They need a wallet they can launch, operate, and evolve without constantly reworking the foundation. ND Labs is a strong partner for that outcome for four practical reasons.
A trust wallet clone script is a ready-to-launch, white-label wallet foundation that follows mainstream Trust Wallet-style UX patterns and core modules, then ships under your brand with the networks and add-ons you scope for your MVP.
Secure on-device key storage, PIN/biometrics, clear signing UX, send-flow protections against common address risks, and a secure release process with testing and a pentest plan before major milestones.
Choose the packaged route when you need speed and more customization control; choose platform-style white label when you want configuration-first predictability. The right decision comes from your platform + chain scope and your need for roadmap control.